The symmetric algorithm uses a key. Given a plaintext and a key, the encryption produces a ciphertext that is roughly the same length as the plaintext. When decrypting, the read key is the same as the encryption key.
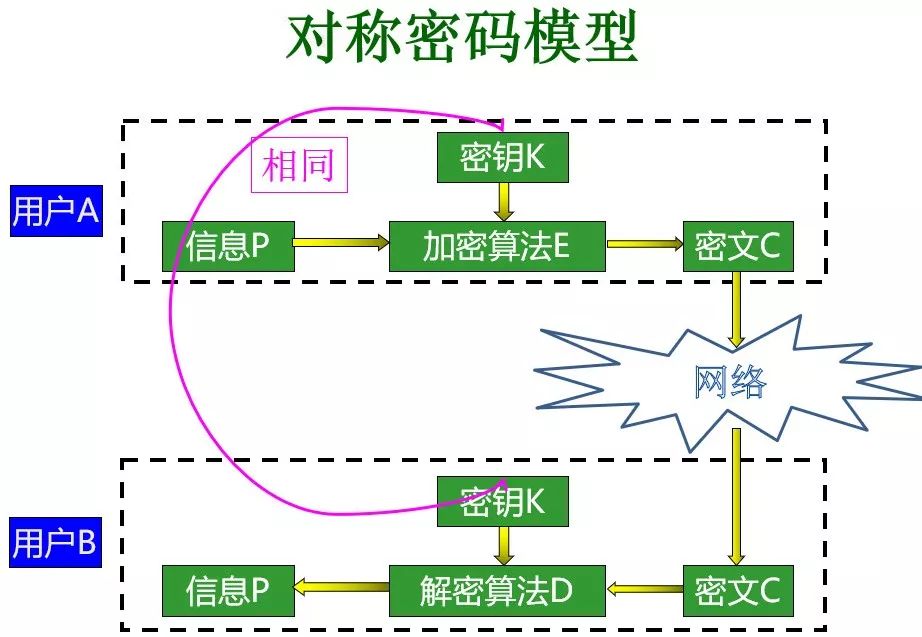
Symmetric encryption example
Common symmetric encryption algorithms are DES, 3DES, AES, Blowfish, IDEA, RC5, and RC6.
Advantages and disadvantages of symmetric encryption
Advantages: Faster than public key encryption.
Disadvantages: Cannot be used as authentication, key issuance is difficult
Symmetric algorithms mainly have four encryption modes: electronic codebook mode, encrypted blockchain mode, encrypted feedback mode, and output feedback mode.
Four working modes of symmetric encryption
1. Electronic Code Book Mode (ECB)
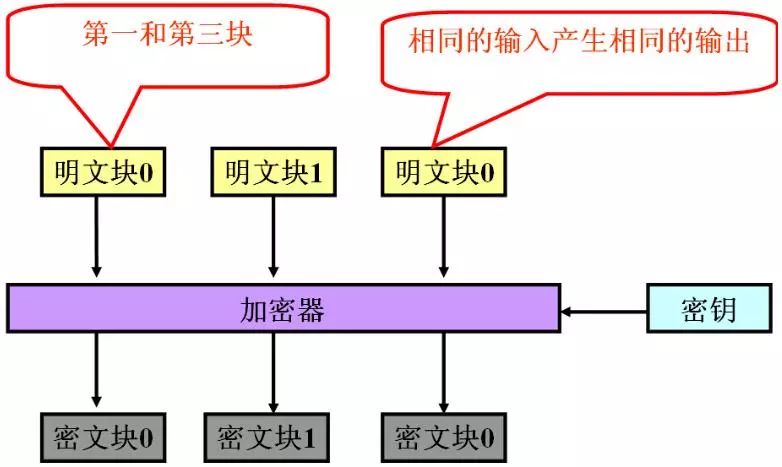
This mode is the earliest and simplest mode. It divides the encrypted data into groups, each of which is the same size as the encryption key, and then each group is encrypted with the same key.
The disadvantage is that the electronic codebook mode encrypts all blocks of the message with one key. If the plaintext block is repeated in the original message, the corresponding ciphertext block in the encrypted message is also repeated. Therefore, the electronic codebook mode is suitable for encrypting small messages. .
Key points
Data grouping, each group has the same length as the key length
Each group is encrypted separately
Applicable to encrypted small messages
advantage
simple;
Conducive to parallel computing;
The error will not be transmitted;
Disadvantage
Cannot hide the pattern of plaintext;
Probably attacking plaintext;
2, encrypted block chain mode Cipher Block Chaining (CBC)
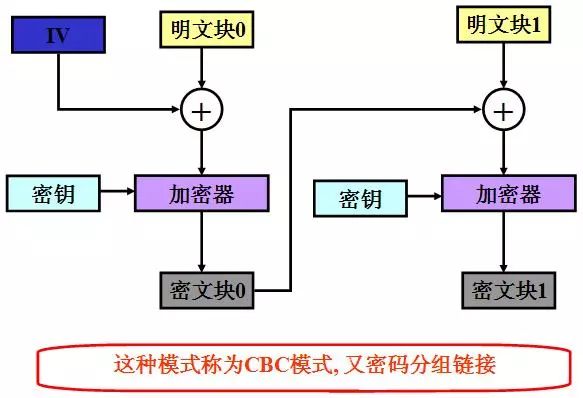
The CBC mode encryption first divides the plaintext into fixed-length blocks, and then XORs the ciphertext outputted by the previous encryption block with the next plaintext block to be encrypted, and then encrypts the result with the key to obtain the ciphertext. When the first plaintext block is encrypted, an initial vector is required because there is no encrypted ciphertext before. Different from the ECB method, through the connection relationship, the ciphertext and the plaintext are no longer one-to-one correspondence, which is more difficult to crack, and overcomes the attack that may achieve the purpose as long as the simple ciphertext block is changed.
Key points
Data packet with the same length as the key
Initialization vector of the same length
After the initialization vector and the ciphertext are suppressed, the encryption is performed again, and the result is re-encrypted with the next data block. And so on.
Features better security
advantage
Not easy to actively attack;
Better security than ECB;
Suitable for transmission of long messages;
It is the standard for SSL and IPSec.
Disadvantage
Not conducive to parallel computing;
Error transfer
Need to initialize vector IV
3. Encrypted feedback mode Cipher Feedback Mode (CFB)
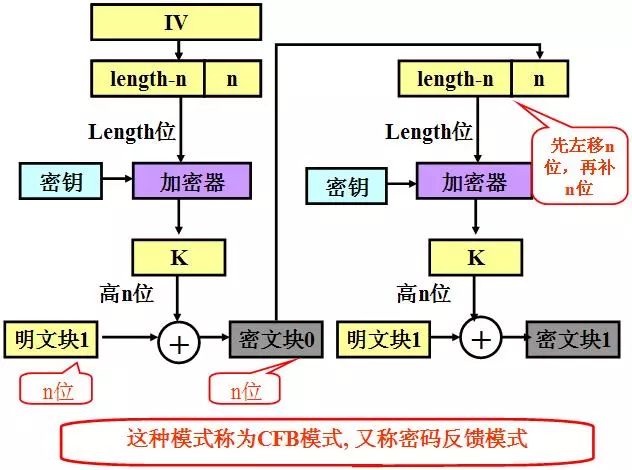
Encryption for character-oriented applications uses stream encryption, and an encrypted feedback mode can be used. In this mode, the data is encrypted with smaller units, such as 8 bits, which is less than the defined block length (usually 64 bits).
The encryption steps are:
Use a 64-bit initialization vector. The initialization vector is placed in the shift register and encrypted in the first step to generate a corresponding 64-bit initialization ciphertext;
The leftmost 8 bits of the initialization vector are XORed with the first 8 bits of the plaintext to produce the first part of the ciphertext (assumed to be c), and then c is transmitted to the receiver;
The bit of the vector (that is, the contents of the shift register where the initialization vector is located) is shifted to the left by 8 bits, so that the rightmost 8 bits of the shift register are unpredictable data, and the contents of c are filled therein;
Steps 1-3 until all plaintext units are encrypted. The decryption process is reversed.
Key points
Data grouping, smaller data block (8bit here)
The 64-bit vector is shifted to the left by 8 bits, and the ciphertext height 8 (c) obtained by the previous round is added.
Key and vector encryption
k high 8 bit and plaintext XOR get the next round of ciphertext
advantage
Hidden plaintext mode;
The block cipher is converted to a streaming mode;
Can encrypt and transmit data smaller than the packet in time
Disadvantage
Not conducive to parallel computing;
Error transmission: one plaintext unit damage affects multiple units;
Unique IV (initialization vector);
4, output feedback mode Output Feedback Mode (OFB)
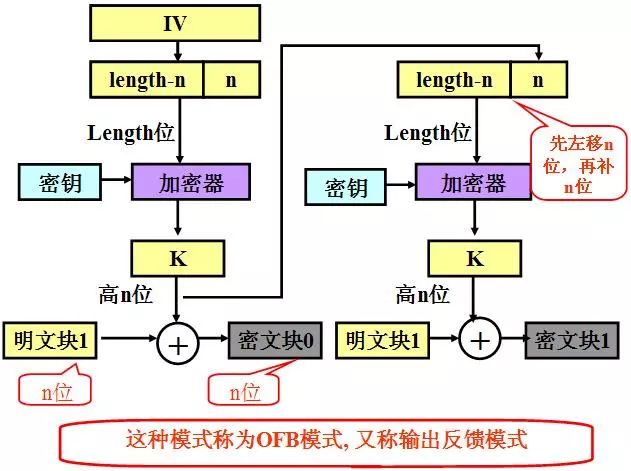
The output feedback mode is similar to CFB. The only difference is that the ciphertext in CFB is filled in the next stage of the encryption process. In OFB, the input of the initialization vector encryption process is filled in the next stage of the encryption process.
Key points
Similar to cfb, the second step is different. The amount of feedback transmission becomes the upper 8 bits of k
Data grouping, smaller data block (8bit here)
The 64-bit vector is shifted to the left by 8 bits, and the k-high 8 (c) bit obtained by the previous round is added.
Key and vector encryption
k high 8 bit and plaintext XOR get the next round of ciphertext
advantage
Hidden plaintext mode;
The block cipher is converted to a streaming mode;
It can encrypt and transmit data smaller than the packet in time;
Disadvantage
Not conducive to parallel computing;
Active attacks on plaintext are possible;
Error transmission: one plaintext unit damage affects multiple units;
High temperature thermocouple slip ring with German and Japanese imports of key materials, can be used in high temperature environment rotate 360 degrees to transmit current and thermocouple signal, can be long-term stability in 100 ~ 250 ℃ high temperature environment, it is mainly used for hot roller, the high temperature environment, such as heating device, suffered long-term complex field practice test, transmission performance is stable and the quality.
High Temperature Slip Ring,Taidacent Slip Ring,Slip Ring Capsule,Fiber Brush Slip Ring
Dongguan Oubaibo Technology Co., Ltd. , https://www.sliprobs.com