We know that in the world of cryptocurrency, private keys represent assets, and the forgetting or theft of private keys is devastating to anyone. In history, many people lost their early days because they forgot their private keys. Invested in cryptocurrencies, some even lost hundreds of millions of assets.
As for the solution of private key security, one is cold storage, and the other is multi-signature technology.
This article will discuss the application of multi-signature technology. Generally, there are two types of multi-signature technologies. One is N-of-N, which requires all private key holders to sign to make the transaction effective. Only the key can control the asset. The commonly used N-of-N multi-signature schemes include 2-of-2 and 3-of-3.
Another type of scheme is N-of-M (where N is less than M), that is, among the M private keys, if at least N private keys are signed, the transaction can take effect. This kind of scheme is also a type of scheme commonly used by companies in the currency circle. The most commonly used scheme is 2-of-3.
However, these multi-signature schemes also introduce great risks, such as the loss of one of the private keys (an accident occurs to one of the holders), or the greed of a private key holder to other holders When the attacker issues a threat, the related assets will be in danger of being lost. We can collectively call this kind of inability to use assets as paralysis.
It seems to be a paradox that it is necessary to be well protected from hacker attacks and to prevent the inability to use assets.
So is there any solution?
Ari Juels, a professor of computer science from Cornell University (one of the proponents of the proof-of-work mechanism), Iddo Bentov, a postdoctoral fellow at Cornell University, Fan Zhang, a doctoral student in computer science at Cornell University, and Phil, a doctoral student in computer science at Cornell University Daian co-proposed a technique called Paralysis Proofs, which enables new possibilities for multi-signature schemes.
The following is the integrated translation (note: "we" in it refers to researchers at Cornell University):
From the gold treasure buried in the "Treasure Island" to the seven missing Faberge eggs, lost and stolen treasures have always been the stuff of legend. However, in the Bitcoin world, there are no princesses, dragons or pirates, and there is not much romance here. The loss of wealth is often just because the private key on the laptop is lost, or the note with the private key printed or copied by oneself is lost, or it is looted by hackers.
Key management is critical in any cryptosystem. Cryptocurrencies like Bitcoin and Ethereum are no exception. Loss or theft of private keys can be catastrophic, and handling private keys well is a very difficult thing. Users need to protect their private keys from theft by crafty hackers, while at the same time securing them properly to prevent loss of assets. Key management is especially challenging in business scenarios, where no one typically trusts fully controlled resources.
Generally speaking, we use multi-signature (mulTIsig) technology to manage the private keys of cryptocurrencies. This is a powerful method. Simply put, it is to allow multiple users to keep a private key, and to conduct transactions, you need one of them. Several private keys to sign. This method of key distribution is also known as secret sharing.
We published a paper addressing a serious problem with secret sharing schemes in general, especially in the cryptocurrency space. We call this problem the paralysis problem.
How does secret sharing lead to the paralysis problem?
A few months ago, an acquaintance asked us a simple, but very interesting question, and it was a great example of a real-world key distribution challenge.
The friend, who goes by the pseudonym Richie here, shares ownership of a large amount of bitcoin with two of his business partners. And they naturally don't want any one of them to be able to sneak these bitcoins away. They want to make sure that these bitcoins can only be used with the consent of everyone. There is an easy solution, right? They could use a 3 of 3 multi-signature scheme, and then all three would need to sign to be able to spend those bitcoins. Problem seems to be solved! But is it really so?
Obviously, the story doesn't end here. Of course, Richie and his partners are also concerned about the situation where one of them loses the private key. For example, the device that stores the keys could fail, the keys could be deleted by mistake, or someone had some very unfortunate situation (such as a car accident) and one of the partners lost their private key. The end result is that all bitcoins are completely lost!
It's not the only bad scenario, Richie and his partners may also have different views on how to spend the money and can't come to an agreement either. Worse yet, assuming one of the partners is malicious or greedy, she could blackmail the others (in exchange for funds) by withholding parts of her keys. In this case, bitcoins may also be lost temporarily or permanently.
The term "paralyzed" is used here to denote any embarrassing situation where Bitcoin cannot be spent. Unfortunately, N-of-N multi-signature schemes cannot solve the paralysis problem. In fact, it makes the problem worse because losing either key would be fatal.
For this reason, we need to meet the goals of Richie and her partners while avoiding a paralyzing situation that requires everyone to agree to spend these bitcoins, which seems impossible! Suppose we have an N-of-N multi-signature scheme, and to complete a transaction, we obviously need to get all partners to agree to sign. If (N-1) partners can somehow gain access to Bitcoin if one partner's key is lost, they can simply pretend that one of the keys has been lost and Get funding. In other words, what we actually started out with was a (N-1)of-N multi-signature scheme, which created a contradiction.
Richie's problem seems to have left us in a state of paralysis. ... ..
resolve paradox
Thanks to the emergence of two powerful technologies (blockchain and trusted hardware), notably Intel SGX, it turns out that we can actually solve this paradox. We can effectively do this in a general setting, for the first time ever, as far as we know. To this end, we have introduced a new technology called the Paralysis Proof system
As you will see, in the Ethereum platform, we can implement this proof-of-crisis system relatively easily, we only need to use a smart contract, and we don't need Intel SGX. We provide examples of Ethereum contracts in our paper. However, the scripting constraints that exist in Bitcoin make it necessary to use SGX devices and introduce some technical challenges.
A simple understanding of the paralysis proof system
The general principle is fairly simple. A trusted third party that keeps all keys in escrow. If one or more parties are unable or unwilling to sign the transaction, this results in the paralysis condition described above, and the others produce a paralysis proof that this is the case. Given this proof, the third party uses the key it holds to authorize the transaction.
However, if we brought in a trusted third party, obviously, we would not be able to achieve the security goals that Richie and his friends proposed. Because one party can control all the private keys!
And this is where SGX comes into play. SGX applications that behave basically like trusted third parties with predetermined constraints. For example, it can be programmed so that a transaction can only be signed if a valid proof is provided. (In this sense, SGX applications behave very similarly to smart contracts.) Thanks to SGX, we can ensure that Bitcoin assets are accessible to the majority of private key holders in the event of a provable paralysis.
some technical details
Of course, even considering this magic of SGX, we still need to ensure that the generation of the Paralysis Proof is legitimate. We don't want Richie's partners to be able to "accuse" him, falsely claiming he is dead, for example by launching an eclipse attack on a host running an SGX application. Happily, the blockchain itself provides a powerful way to transmit messages and let someone know that the transmitter is alive. In order to implement a proof-of-crisis system on the Bitcoin network, we take advantage of this fact along with a few tricks. For simplicity, we will focus on the problem of inaccessible keys and leave other forms of paralysis aside for now.
A paralysis proof will be constructed to prove that a party P does not respond in time (cannot sign the transaction). The system issues a challenge in which the "charged" party must respond to what we call a "life signal." If no vital signs respond to the challenge for a predetermined period of time (eg 24 hours), the absence constitutes proof of paralysis.
For Bitcoin, the life signal of Party P can be in the form of a negligible amount (such as 0.00001 BTC) of Bitcoin UTXO, which can be sent by Party P (thereby proving that she still exists), or sent through pk_SGX ( But you need to wait for the delay before you can do it). Note that sk_SGX is only known by the SGX application.
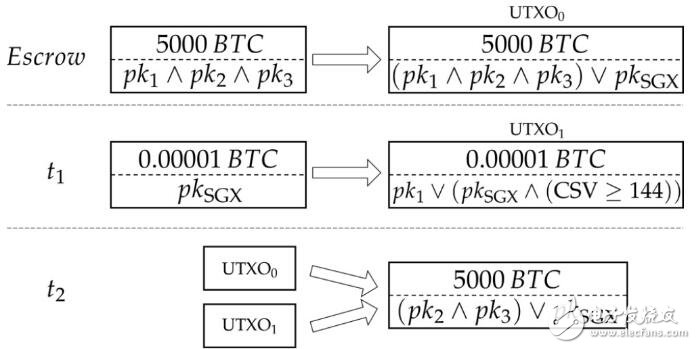
Let's take three more partners as an example. Suppose they each have a key pair (sk_i, pk_i). First, they will host their own bitcoin funds (let's say 5000 BTC) to the spendable output UXTO_0, which can be used when all three agree, or via pk_SGX. Now, suppose P_2 and P_3 decide to charge P_1. After the SGX application receives the two requests, it will prepare the following two transactions and send them to P_2 and P_3:
t_1 (transaction 1) creates a life signal UTXO_1 of 0.00001 BTC, for which pk_1 can use it immediately, or after a timeout (e.g. 144 blocks, about 24 hours) by pk_SGX;
t_2 (transaction 2) will spend UTXO_0 and the life signal UTXO_1, and send them to an address that can be controlled by pk_2 and pk_3 (or pk_SGX is optional if they want to stay in the crash proof system).
Therefore, the partner accusing P_1 should broadcast t_1 to the Bitcoin network, wait for t_1 to be added to the blockchain, wait for the next 144 blocks, and then broadcast t_2 to the Bitcoin network. During this time, there are two possible outcomes:
· In the case of legal charges, P_1 is indeed unable to use t_1 transactions, and once the t_2 transaction is confirmed by the network, P_2 and P_3 will gain access to Bitcoin. This ensures the availability of BTC funds.
However, in the case of malicious allegations, the above scheme ensures that P_1 can appeal within 144 blocks. To do so, P_1 can spend UTXO_1 using that key known only to her. Since t_2 takes both UTXO_0 and UTXO_1 as input, spending t_1 will make t_2 an invalid transaction.
security argument
The safety of the life signal is derived from the use of CheckSequenceVerify in t_1. In detail, t_2 is only valid if the verified part of each input (called ScriptSig in Bitcoin) is correct. The verification part produced by the SGX enclave device to spend the escrow fund takes effect immediately, but only after the t_1 transaction is included in the Bitcoin blockchain (144 blocks wait due to CSV conditions), the verification part that costs t_1 will work. Therefore, setting the timeout parameter to a large value serves two purposes: (1) to give P1 sufficient response time, and (2) to ensure that attackers cannot replace the Bitcoin blockchain by making their own chains.
Application on the Ethereum platform
The above mentioned examples are all about Bitcoin, but the paralysis proof system can not only be applied to Bitcoin. For a smart contract platform like Ethereum, its implementation will be simpler. letter SGX hardware requirements.
The reference implementation code we gave is only 117 lines, and the following is the main logic:
funcTIon spend(uint256 proposal_id) public {
// Get rid of any paralyzed keyholders
prune_paralyzed_keyholders();
require(is_keyholder(msg.sender));
require(proposal_id "proposals.length);
// add sender's signature to approval
proposal_sigs[proposal_id][msg.sender] = true;
// if enough proposers approved, send money
uint num_signatures = 0;
for (uint256 i = 0; i < keyholders.length; i++) { if (!paralyzed[keyholders[i]]) { if (proposal_sigs[proposal_id][keyholders[i]]) { num_signatures++; } } } if (( num_signatures) > = required_sigs) {
if (!proposals[proposal_id].filled) {
proposals[proposal_id].filled = true;
proposals[proposal_id].to.transfer(proposals[proposal_id].amount);
}
}
}
funcTIon remove(address accused) public {
// Get rid of any paralyzed keyholders (prevent paralyzed requester)
prune_paralyzed_keyholders();
// both requester and accused must be keyholders
require(is_keyholder(msg.sender));
require(is_keyholder(accused));
// There shouldn't be any outstanding claims against accused
require(!(paralysis_claims[accused].expiry > now));
// Create and insert a Paralysis Claim
paralysis_claims[accused] = ParalysisClaim(now+delta, false);
NewAccusaTIon(accused, now + delta); // Notify the accused
}
function respond() public {
require(paralysis_claims[msg.sender].expiry > now);
paralysis_claims[msg.sender].responded = true;
}
The complete contract code, readers can visit: https://github.com/pdaian/paralysis_proofs View
other applications
In addition to cryptocurrency applications, paralysis proof technology can also be applied to credential decryption. You can use a paralysis proof to create a proof for releasing a file, allowing a person or group of people to decrypt it. Here are some examples of applications where these strategies can be implemented with a combination of blockchain (censorship resistance channels) and SGX:
Daily spending limit: ensures that funds that can be spent from a public pool in 24 hours will not exceed a pre-agreed amount (say 0.5 BTC, the authors discussed some practical limits in the original paper)
Event-driven access control: Using an oracle such as the Town Crier system (actually the first public-facing SGX application), this can condition access control policies on real-world events. For example, by providing exchange rate data feedback, the daily spending limit may be denominated in USD rather than BTC. One could even use natural language processing in principle to respond to real-world events. For example, if the author of a document with leaked information is indicted by the US federal government, a journalist could declassify the document.
· Escalation Threshold Requirements: Participants can be added and removed from the access structure if a pre-set number of participants agree, i.e. changing the rules regarding the number of authorized participants. For example, a k-of-N multi-signature scheme can be changed to a (k+1)-of-(N+1) signature scheme. In conventional secret sharing schemes, this is not possible to upgrade because a group of authorized participants can always reconstruct the private keys they hold. However, if the SGX application controls the decryption keys, it can monitor the blockchain to determine if participants have voted to upgrade, and if they are recorded on the blockchain, the votes will not be suppressed.
Existing security risks and future improvements
Of course, when the trusted SGX hardware is introduced, the risk of side channel attack (side channel attack) will also be introduced, which is also the main problem encountered by this scheme. In future work, we will explore to mitigate this Attack techniques. For example, in a system that allows N-of-N multi-signature schemes that can be downgraded to (N − 1)-of-N multi-signature schemes, it is possible to have an SGX enclave application store and conditionally release A single private key, rather than controlling one master private key. This will limit the harm caused by side channel attacks. We can also store keys in multiple SGX enclaves, which helps mitigate the risk of node failure, while also helping To recover from node failure, this is another work that needs to be studied.
appendix
In the paper, we discussed a lot of interesting extensions, here are two of them:
Proof of paralysis proposed by covenants
As mentioned above, due to the scripting constraints of Bitcoin, applying crash proofs on the network requires the use of SGX devices. In fact, we also propose a "slightly less efficient" approach that does not require trusted hardware, which requires the use of a proposed Bitcoin feature called covenants. However, the complexity of using this approach is significantly higher than the SGX trusted hardware approach (both conceptually and in terms of on-chain complexity), so we do not recommend it.
Another better solution
In the previously mentioned example, funds could be used by pk_SGX alone, but importantly, this is not the only option. In fact, people can make a trade-off between security and paralysis tolerance to best meet their needs.
For example, if three partners only wish to tolerate at most one missing private key, what they can do is transfer funds to a 3-of-4 multi-signature address where the fourth participant is the SGX enclave device . If all were alive, they could use Bitcoin funds without needing SGX. If one of the partners has an accident and he cannot sign, if the remaining two partners can show the paralysis proof, the SGX enclave device will release its private key. Therefore, even if an attacker breaches the private key held by the SGX device through a side-channel attack, he cannot spend these bitcoin funds, with the only exception that the two partners are in collusion with the attacker.
The hendlight wiring harness apply for household appliance, automotive, motocycle, bus, bike, truck, medical equipment.
Yacenter has experienced QC to check the products in each process, from developing samples to bulk, to make sure the best quality of goods. Timely communication with customers is so important during our cooperation.
If you can't find the exact product you need in the pictures,please don't go away.Just contact me freely or send your sample and drawing to us.We will reply you as soon as possible.
Headlight Wiring Harness,Headlight Harness,Headlamp Wiring Harness,Headlight Wiring Kit
Dongguan YAC Electric Co,. LTD. , https://www.yacentercns.com