The terminal of the Internet of Things is goods, and people's lives and work are inseparable from thousands of various objects around them. This article discusses technologies related to the identification of people by the Internet of Things.
The nature of the Internet of Things includes automatic identification
The essence of the Internet of Things can be summarized in three aspects: one is interconnection; the second is identification and communication features, that is, the "things" included in the Internet of Things must have the function of automatic identification and communication (M2M); the third is Intelligent features, that is, the network system should have the characteristics of automation, self-feedback and intelligent control. Among them, "recognition and communication features" and "intelligent features" are inseparable from the identification of objects and related personnel. The objects have the function of automatically identifying and communicating with things, and the Internet of Things platform, objects, and people can automatically identify each other.
This shows that automatic identification occupies an important position in the Internet of Things, and biometric technology is one of the most important means to achieve automatic identification. In the field of Internet of Things applications, biometrics technology is widely used in various industries such as green agriculture, industrial monitoring, public safety, urban management, telemedicine, smart home, smart transportation, and environmental monitoring.
The concept of electronic identification services
Electronic identification (EID) applications have a long history. From the beginning of the computer, the use of passwords to verify the identity of computer users is the earliest EID application. With the development of social economy, the EID application has gradually expanded to the fields of e-government and people's livelihood, responsible for the identification of citizens, government officials and mobile terminals.
Like the Internet, all information that the Internet of Things can identify users and objects is represented by a specific set of data. This particular set of data represents a digital identity, and all authorizations for users and objects are also authorizations for digital identities. How to ensure that the user operating with a digital identity is the legal owner of the digital identity, that is to say, to ensure that the physical identity of the user corresponds to the digital identity, EID service is to solve this problem. As the first gateway to the Internet of Things, the importance of EID services is self-evident.
In the real world, the basic methods of user identity authentication can be divided into three types: speak the information you know, display what you have, and provide unique biological characteristics. The identity authentication method in the Internet of Things is consistent with that in the real world. The means of identity authentication in the Internet of Things include: 1. Enter confidential information, such as the user ’s name, password, or encryption key; 2. Display the physical objects such as access cards, keys, or tokens. Recognition; Third, the use of biological features, such as fingerprints, sounds, retina and other recognition technologies to uniquely identify users.
Electronic identity recognition based on biometrics
Biometric-based EID refers to an electronic identification technology that distinguishes individual organisms by identifying the biological characteristics of the organisms (specifically, people). At present, there are many research fields of biometrics, including speech, face, fingerprint, palm print, iris, retina, body shape, keyboard typing, signature, etc. For the Internet of Things, we selected four biometrics of face, voice, fingerprint and iris as the identification basis of the biometric-based EID service.
Face recognition
The advantages of face recognition are its naturalness and characteristics that are not noticed by the individual being tested. However, face recognition technology is very difficult, and is considered to be one of the most difficult research topics in the field of biometric recognition, even artificial intelligence.
Speech Recognition
Voice recognition uses recording equipment to continuously measure and record the waveform and changes of sound, and matches the sound collected on the spot with the registered sound template to determine the identity of the user. The recognition accuracy of this recognition technology is not high because of technical problems.
Fingerprint recognition
Fingerprint recognition has a long history as a recognition technology and can reliably confirm a person's identity. However, fingerprints of certain people or groups are difficult to recognize because of fingerprint characteristics, and often cannot be recognized when the finger points to sweat or is contaminated.
Iris recognition
The accuracy of iris recognition technology is several to dozens of orders of magnitude higher than other biometric authentication technologies. The disadvantage of iris recognition is that the user's eyes must be aimed at the camera, and the camera scans the user's eyes at close range, which is an intrusive recognition method, which will cause some users' disgust.
Application of electronic identification in smart city
Driven by the government, the Internet of Things will be widely used in various fields of smart cities to improve government efficiency. The application of EID service in the field of Internet of Things has solved the problem of identification of smart cities. From the definition of the Internet of Things, EID services are the prerequisite for the development of the Internet of Things. To achieve intelligence and automation, the Internet of Things must first determine the legal identity of users and their items. All Internet of Things applications for cities require EID services.
ZTE proposes a five-in-one application solution for smart cities, which integrates the most commonly used livelihood activities: household registration, election activities, driver's license verification, water and electricity services, and medical services. All verification information is stored uniformly, and each institution does not need to collect it repeatedly Citizen data. The comprehensive management plan optimizes citizens' lives and makes the city smarter.
The account registration information can prove the citizen ’s identity, and can also be used to check the status data such as nationality, age, blood relationship, etc. The election certificate is the proof that the citizen has the right to vote in an election event; in the Internet of Things environment, the verification of the driver ’s license becomes very important Simple, after the verification terminal is connected to the Internet of Things, online query and offline verification can be performed; water and electricity are the most important living materials for citizens. At present, water and electricity supply belong to different systems, and meter reading and payment are inconvenient. After the management of the Internet of Things, water meters, electricity meters and gas meters are all intelligent, which will greatly facilitate the lives of citizens and improve management efficiency; in the Internet of Things, medical instruments can be transformed into smart sensors, through medical intelligent sensors at both ends of the hospital and home Connect hospitals and families, establish remote medical centers, and conduct remote consultation, remote monitoring, and remote diagnosis.
The smart city five-in-one application solution is centered on EID services, using smart card technology to achieve biometrics, and making the city smart through multiple links such as identity information collection, network transmission, unified management and business processing.
smart card
The scheme uses a smart card with a CPU to store four types of data: user ID, user password, digital certificate, and private key, as well as key business information such as account registration, election certificate, driving license, water and electricity services, and medical services. The cryptographic algorithm, public key certificate and corresponding private key are stored in the smart card, and the signature and encryption are performed in the smart card. The private key is not out of the card, and the confidential content cannot be copied, and double strong factor authentication is used-using biometrics instead of PIN code authentication .
The components of the smart city plan are shown in Figure 1.
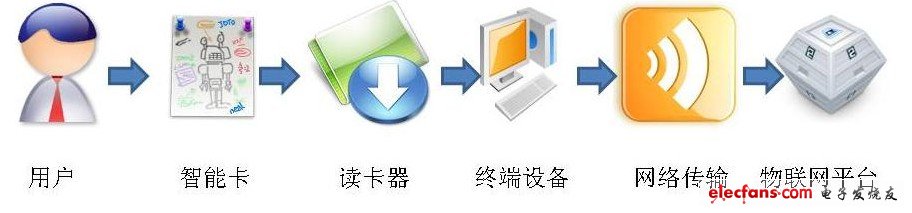
Figure 1 Relationship between smart card related devices, users, and IoT platforms
Integrated biometrics
Each of the four biometrics technologies has advantages and disadvantages. Therefore, the electronic identity recognition service uses a comprehensive biometrics method to integrate four types of biometrics into two groups. One group is natural recognition, including face recognition and voice recognition, and the other group is accurate recognition, including fingerprint recognition and iris. Identify. The electronic identity recognition service system is configured to select one or two combinations from these two groups for identification. Integrated biometrics can improve the accuracy of identification, while improving user-friendliness and increasing the ease of use of the system.
Architecture
The system of the five-in-one smart city application scheme uses a 4-layer structure, as shown in Figure 2.
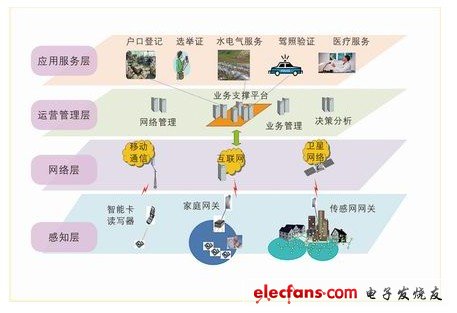
Figure 2 4-layer structure diagram of a five-in-one smart city application
The fourth layer application service layer is composed of IoT applications, services and users. It combines with industry needs to realize the intelligent application of IoT, including the citizen information center, citizen service system, and smart card management system. These systems enable all citizens and service providers to use a unified portal for access and various management operations through smart cards and biometrics. Service providers include not only government departments such as police stations, election offices, and community offices, but also water supply companies. , Gas and natural gas companies, power companies, hospitals and other medical institutions. The system provides external interfaces for connecting other scalable e-government application systems.
Using biometrics technology can accurately identify citizens' identity, solve the most basic problems of IoT applications, and promote the development of smart cities.
China Restaurant Pos Software ,All In One Pos Systems , Smart Pos Machine Manufacturer
THE Restaurant Pos System DESIGNED TO HELP YOU GROW
Gmaii Food Beverage Pos System`s tablet point of sale system speeds up, simplifies, and automates restaurant operations so you can focus on what`s important.
Gmaii Food Beverage Pos System Register at Press Street
Gmaii Food Beverage Pos System`s Restaurant Pos System at Your Service.
Everything about Gmaii Food Beverage Pos System`s system is designed to help you turn, burn, and earn more efficiently than ever before.
Front and Back of House
Tableside Ordering
Mobile Business Insights
Staff Management
Reporting and Analytics
Customer Support
Customer Loyalty
Customizable Hardware
Integrated payment processing
Online Ordering
Integrated Accounting
Multi-Location Management
Food Beverage Pos System
Restaurant Pos Software ,All In One Pos Systems ,Smart Pos Machine ,Best Pos System For Restaurant
Shenzhen Gmaii Technology Limited , https://www.gmaiipos.com